End-to-End Governance, Risk and Compliance with ZenGRC.
Leverage one platform for all your compliance, audit, risk, third-party risk solutions, and governance and policy management applications.
This email address is being protected from spambots. You need JavaScript enabled to view it. BrochureZenGRC is designed to help business leaders mitigate the risks they know about and prevent the risks they can’t see coming.
ZenGRC offers an established solution to elevate your company’s risk and compliance program to the highest infosec standards. The cloud-based SaaS solution fits your existing GRC program and also evolves to guide you throughout your maturity roadmap. With ZenGRC as the central platform for your organization’s entire infosec ecosystem, you can achieve continuous monitoring and efficient audit management capabilities, as well as customizable, end-to-end risk management that’s built-in — not bolted on.
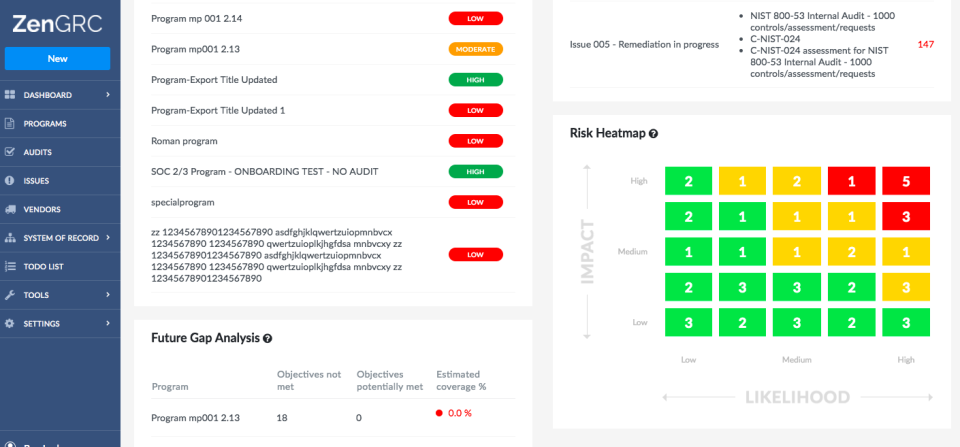
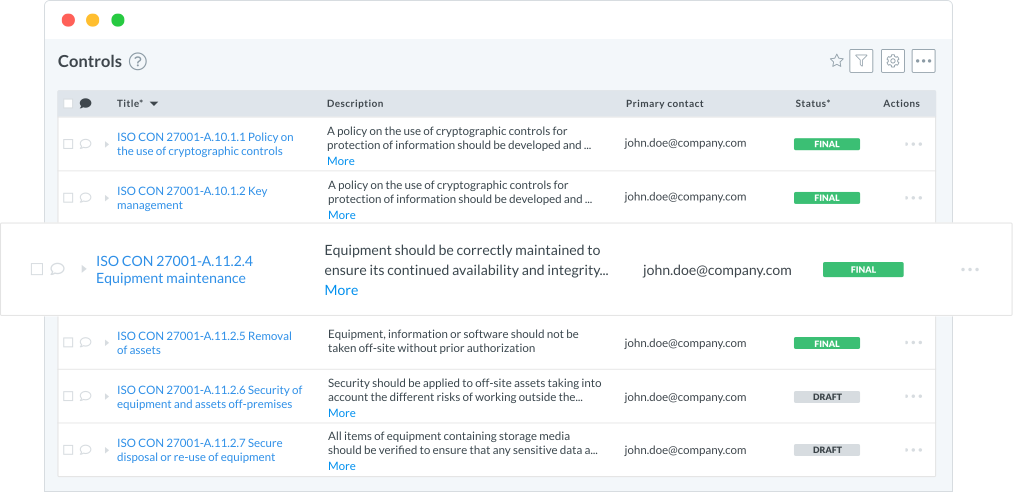
Support the full audit process by gathering evidence and reports based on the right control designs and tests. Ensure audits remain current as your business evolves using live dashboards that let you prioritize audit work based on risk exposure, business objectives and audit committee requests as well as generate dynamic audit reports in Word or PDF format with push-button ease.
Easy evidence collection: Customized, role-based dashboards, project queues and automated notifications make sure audit findings are assigned to the right business owners so issues are addressed and resolved correctly.
Cross-Team collboration: With one-click navigation, audit staff can manage electronic work papers and findings, review notes and get a live view of audit project status and utilization, all of which can be share with other assurance functions, including SOX compliance, enterprise risk, information security, quality control and vendor management.
Expose compliance-related risks with intuitive and automated alerts and workflows so you can catch and remediate risks with real-time updates.
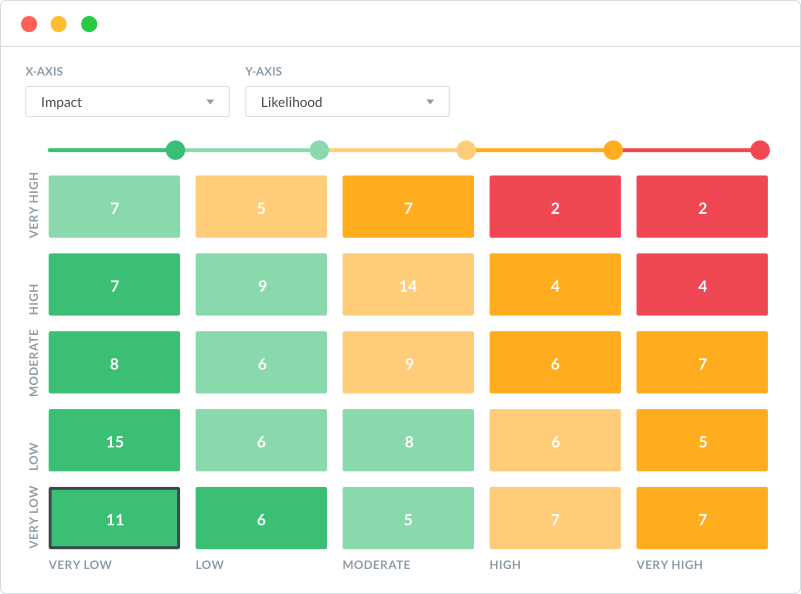
Address Enterprise Risk Management (ERM) and Cybersecurity Risk across threats, vulnerabilities and incidents from one application and communicate current risk status and potential threats through risk heatmaps, dashboards and reports.
Evaluate risks across connections, such as systems, business divisions and controls, using customizable risk calculations with multivariable scoring, including SCF and NIST frameworks, Cyber Risk Catalog and the RISQ Management Enterprise registers, and CIS-RAM Simplified and RISQ calculation methods.
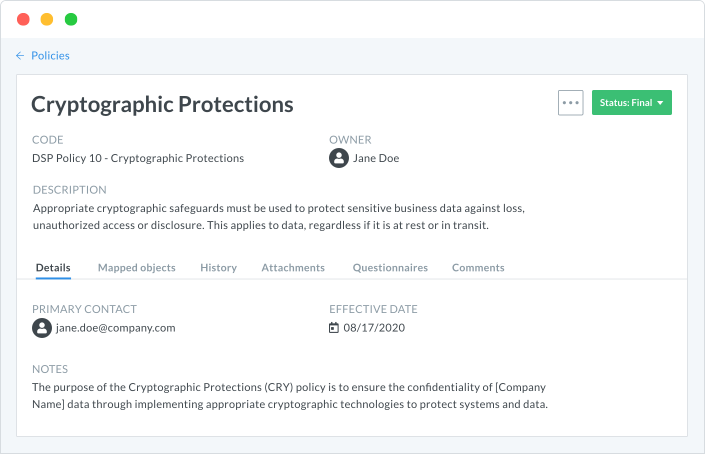
Consolidate policies and procedures and automate routine compliance activities in your organization.
ZenGRC equips your security and compliance teams with a single, integrated experience that reveals information security risk across your business.
It’s hard to see evolving threats unless they’re exposed. ZenGRC shows where risk is changing in your organization.
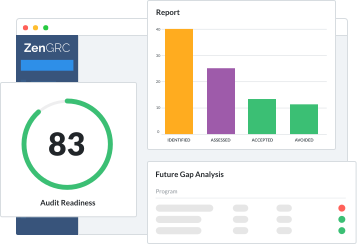
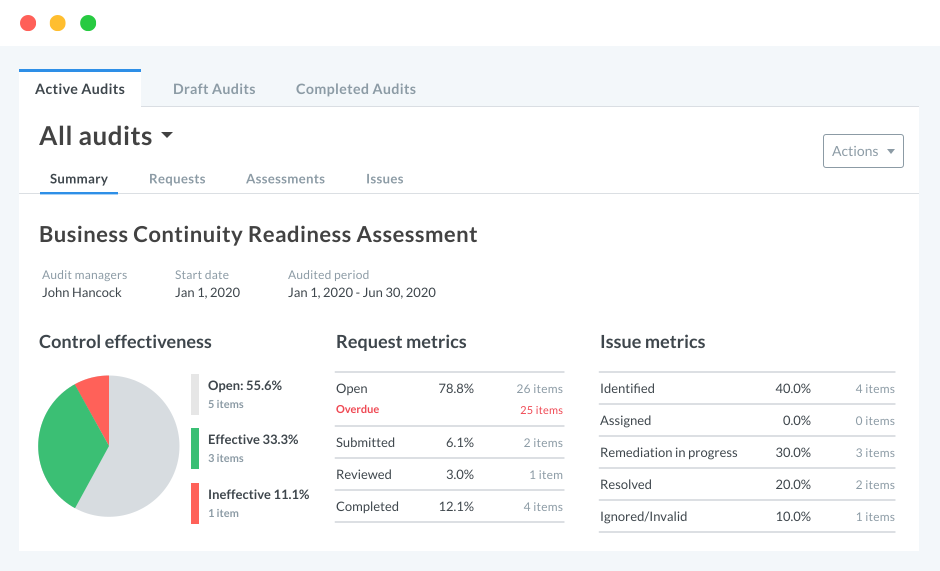
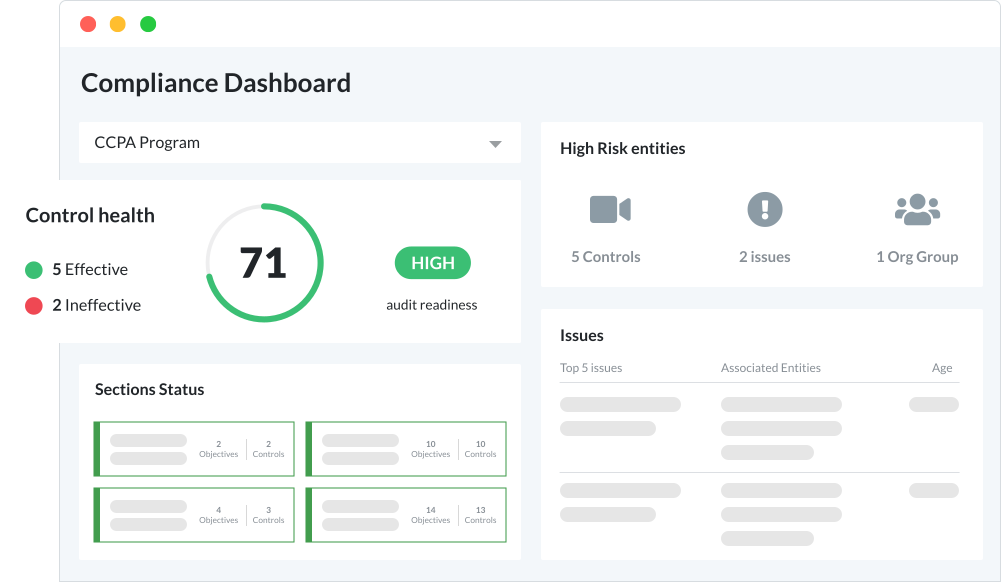
ZenGRC simplifies audit and compliance management with complete views of control environments, easy access to information necessary for program evaluation and continual compliance monitoring to address critical tasks at any time.
Pre-built compliance dashboards provide visibility into completed tasks, open items, reviewer hierarchies, progress, status, pending deadlines and supporting documentation, revealing the health of your company’s compliance and IT information security programs along with a simple way to manage your compliance program.
Save time, increase visibility and improve vendor relationships with streamlined vendor and third-party risk management that automates questionnaires and assessments, eliminating labor-intensive internal tasks.
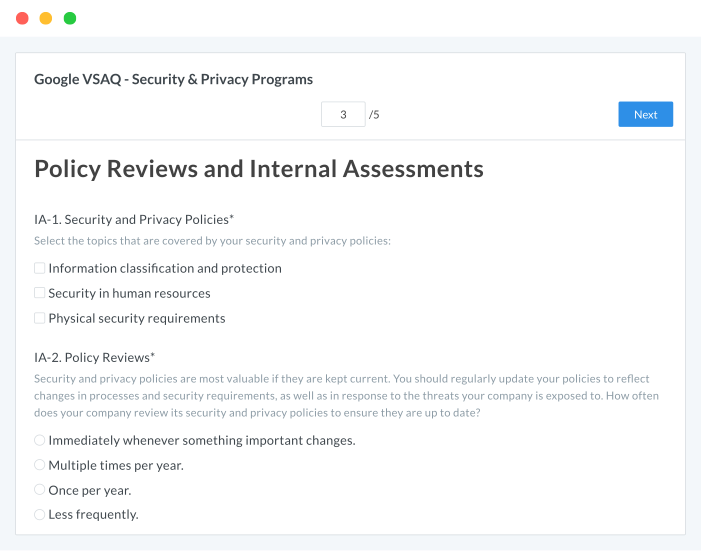
Vendor Questionnaires: Create a more efficient and less manual risk-based approach to vendor management by defining actions for specific questions, which may spawn multiple workflows to ensure issues are addressed.
Business Impact Questionnaires: A more efficient way to gather information, documentation or opinions, questionnaires are designed so that responses lead to cascading questions. A weighing scale in the questionnaire applies a risk score.
Vendor Specific Reporting: Assess and compare vendors by individual responses and risk scores over time and easily report insights to management.
Safeguard your business by planning for worst-case scenarios and potential threats.